Recently, security researchers have discovered a new phishing campaign targeting Gmail users.
This Gmail Phishing Attack Is So Real, It Can Even Fool Professionals
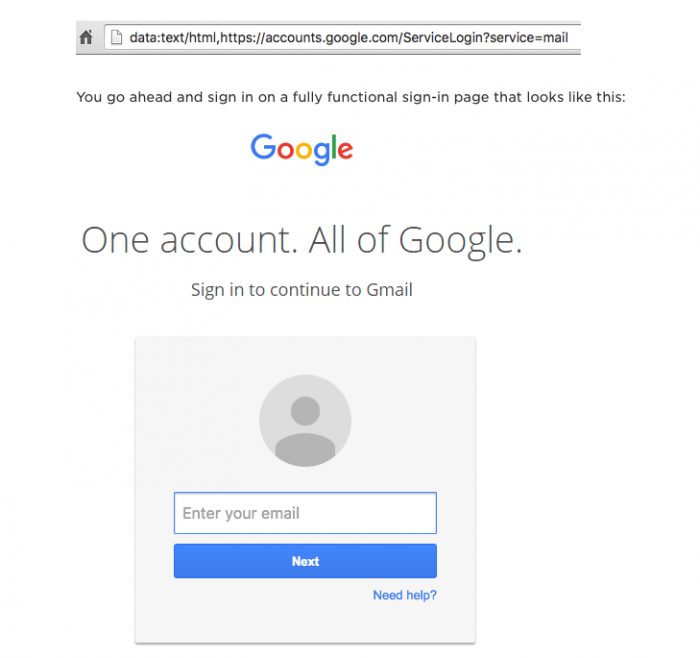
When you talk about phishing, a technique in which a hacker tries to steal personal data from a person or organization, but you think you’re too smart to be deceived. That’s where the problem is: some attacks are more sophisticated and we need a little attention to unmask them. That’s what happened to British comedian Tom Scott. When opening a common email in Gmail, Scott saw that it had a supposed attachment and almost clicked. Before falling into the trap, he realized that the attachment block was blurred due to the high-definition screen he uses and did not click. It did well: the block was actually an image that led to a fake Google login page.
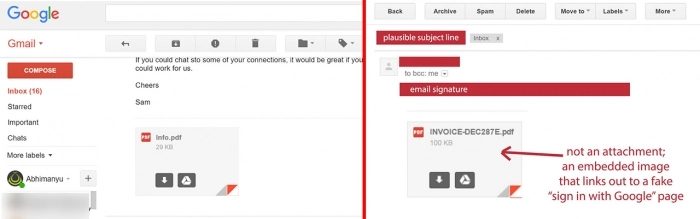
— Tom Scott (@tomscott) December 23, 2016 As we see in the pictures mentioned below, the attachment message is, in fact, quite convincing. If it was not too blurry to be in Gmail, even I would click. The fake login page can be unmasked by the URL: there is a “date:text/html” up front, but anyone who is distracted may not even notice and send their false information to someone who is malicious.
This specific phishing technique was identified by Wordfence earlier this year. As the security firm explains, shortly after the attack, hackers log into your account and spread a custom attack for all your contacts. “For example, they entered a student’s account, took an attachment with a training schedule from an athletic team they participated in, generated the screenshot, wrote an email with a related subject, and sent it to other members of the Time,” explains a user on Hacker News.
How to protect yourself?
The main tip is: be careful. If you get an e-mail from any strange person or someone you do not know, meticulously analyze to see if this is not a very well-done phishing attack. Look at the difference between a real attachment and this one from the tweet:
Also, check the URL of the pages you are accessing. When you sign in to Google, the link in the address bar would be “accounts.google.com” and would be accompanied by the secure “https://” protocol instead of the regular “http”. Also, look for a green padlock next to the URL. Another factor that potentiated the attack was the absence of even the red color in the URL or padlock, which Google usually does for insecure sites that are using the irregular https protocol. In the comparison below, notice that the malicious URL had no color, so it could go undetected without problems. Finally, in Chrome version 56.0.2924, the tech giant Google has posted a “No-safe” warning in the form’s address bar to aid in identification. If your Chrome is up to date, it’s already one more indicator to watch at the time of the attack. Check out the latest activity on your account to see if there are any open logins you do not know about. Also enable 2-step authentication to prevent intrusions, even if the hacker has your password.
Δ